Introduction
We explored a range of commercial and open source obfuscators such as ConfuserEX, ConfuserEX2, DotFuscatorCE, Obfuscar with varying levels of success.
One glaring issue is that none of the obfuscators have great documentation for new comers or experienced developers when things don’t work as expected. Many hours are required to hunt down solutions from places other than the authors repositories.
Visual Studio – Microsoft have bundled the DotFuscator Community Edition with Visual Studio however we are not impressed with the free version as a serious entry point to protect your works. Also we don’t like being pestered to register.
Obfuscar – Probably works but we could not get any exe’s or DLL’s to work after obfuscation and it was just too difficult to find solutions and the authors site appears to have wiped the wiki.
ConfuserEX has a number of forks available and we settled on ConfuserEX-Reborn
And to compliment ConfuserEX we installed ConfuserEX for Visual Studio from Market Place however this crashed Visual Studio 2017 frequently and when you attempt to remove obfuscation from a project it leaves an entry “exec” in the project file that prevents a successful compile. So ConfuserEX for Visual Studio caused more issues than it was worth and we uninstalled it from Visual Studio.
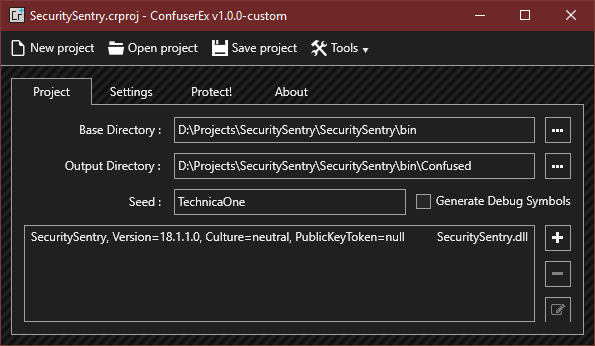
Our final decision was to download the source for ConfuserEX Reborn and dnlib and compile ourselves. The ConfuserEX comes with a very functional GUI that we found was great for building the Ofuscated project and finally protecting your solutions.
ConfuserEX – Reborn
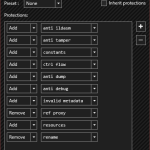
Features
- Supports .NET Framework 2.0/3.0/3.5/4.0/4.5
- Supports Mono (Some feature restrictions apply)
- Symbol renaming (Support WPF/XAML/BAML)
- Protection against debuggers/profilers
- Protection against memory dumping
- Protection against tampering (method encryption)
- Control flow obfuscation
- Constant/resources encryption
- Reference hiding proxies
- Disable decompilers
- Embedding dependency
- Compressing output
- Extensible plugin API
- Many more are coming!
Protections
So let’s say you have the following output from your project with a couple of dependant libraries:
- TheWorldsGreatest.exe
- MyCommonLibrary.dll
- MyHTMLViewer.dll
We use ILMerge to merge the two dll’s into TheWorldsGreatest.exe.
As a result we just need to obfuscate and deploy a single exe.




 (1 votes, average: 5.00 out of 5)
(1 votes, average: 5.00 out of 5)